The post Generative AI in the Corporate World: Unlocking Promise and Overcoming Challenges appeared first on 333dots it consulting in frisco.
]]>Shaping the Future of Soft Skills Training: The Role of Generative AI
Improving the cooperative energy among delicate abilities, generative computer-based intelligence, and keen mechanization offers a groundbreaking chance to essentially reshape business tasks. Through capably mixing the ability of human limits with the effectiveness of IA, undertakings can achieve increased edges of efficiency, development, and extension. As these particular yet correlative components meet up, they make a dynamic and cooperative relationship that can possibly reshape the actual groundwork of how ventures work and flourish in the present consistently developing business climate.
Future of Soft Skills Training The Role of Generative AI
Delicate abilities, those immaterial and relational characteristics that envelop correspondence, sympathy, joint effort, and versatility, have for some time been viewed as basic parts of powerful initiative and fruitful collaboration. Their characteristic worth lies in their capacity to encourage significant human associations, span holes in understanding, and explore complex difficulties with artfulness. With regards to this groundbreaking intermingling, delicate abilities take on a much more urgent job. They act as the scaffold that interfaces the human aspect with the mechanical headways addressed by generative simulated intelligence and smart robotization.
Generative simulated intelligence, then again, presents another range of potential outcomes through its ability to break down huge measures of information, recognize designs, and create bits of knowledge that were already distant. This innovation can quickly handle data, foresee drifts, and give priceless proposals that guide dynamic cycles. The mixture of delicate abilities and generative man-made intelligence makes an agreeable transaction where human instinct and compassion meet with information-driven experiences, prompting informed decisions that balance the insightful with the close to home.
Wise mechanization, with its capability to execute routine undertakings with speed and accuracy, further supplements this cooperative energy. Via mechanizing dreary cycles, ventures can divert their HR toward key drives that request innovativeness, decisive reasoning, and critical thinking abilities — regions where human skill genuinely sparkles. The organization between delicate abilities, generative computer-based intelligence, and canny robotization enhances the potential for development, as human resourcefulness is freed from everyday errands, empowering an emphasis on more significant level undertakings that drive development and the upper hand.
The way to understand the maximum capacity of this intermingling includes a thorough comprehension of every part’s assets and their amicable coordination. As organizations set out on this extraordinary excursion, it becomes basic to support and develop both the delicate abilities of their labor force and the specialized capacities of their simulated intelligence frameworks. This requires an essential way to deal with preparing, improvement, and transformation, guaranteeing that the labor force is outfitted with the relational abilities expected to team up consistently with computer-based intelligence innovations.
Also, this groundbreaking union conveys moral contemplations that warrant cautious assessment. The dependable and moral utilization of artificial intelligence and robotization should be focused on to stay away from potentially negative side effects and to maintain values like straightforwardness, reasonableness, and responsibility. As organizations face the force of these advancements, they should likewise be aware of possible predispositions, information security concerns, and the in general cultural effect of their choices.
Let's delve into the concept of Generative AI:
Generative man-made intelligence, a part of computerized reasoning innovation, has the capacity to make a wide exhibit of content kinds, including text, pictures, sound, and engineered information. The new upsurge of interest encompassing generative artificial intelligence can be credited to its easy-to-use interfaces, which speed up the quick age of top-notch text, designs, and recordings in only seconds.
It’s significant that this innovation isn’t completely new. The underlying foundations of Generative computer-based intelligence can be followed back to the 1960s with the rise of chatbots. Be that as it may, a critical jump happened in 2014 with the presentation of Generative Ill-disposed Organizations (GANs), a classification of AI calculations. This progression enabled generative computer-based intelligence to create surprisingly credible pictures, recordings and sounds that look similar to genuine people.
This newly discovered capacity has opened a scope of chances, for example, further developed film naming and vivid instructive substance. In any case, it has additionally prodded worries about profound fakes — carefully controlled pictures or recordings — and the potential for pernicious network protection assaults on organizations. These assaults might include tricky solicitations that handily imitate correspondence from a representative’s boss.
So, how does generative AI function?
Generative man-made intelligence starts with a brief, which can appear as text, pictures, recordings, plans, melodic notes, or any info that the simulated intelligence framework can process. Different computer-based intelligence calculations then, at that point, create new happiness because of this brief. This content could envelop articles, answers for issues, or even similar creations made from pictures or sound accounts of people.
In the underlying periods of generative artificial intelligence, clients were expected to submit information through APIs or explore multifaceted strategies. Designers needed to find out more about particular apparatuses and make applications utilizing dialects like Python.
Nonetheless, trailblazers in the domain of generative simulated intelligence are right now growing more natural client encounters that empower clients to convey demands utilizing ordinary language. Following the underlying result, clients additionally have the capacity to tweak the outcomes by offering input in regards to the ideal style, tone, and different traits they wish the created content to exemplify.
The Combination of Delicate Abilities Preparing with Generative Computer-based Intelligence By blending the force of delicate abilities, generative man-made intelligence, and IA capacities, associations can tackle the aggregate qualities of these components to lay out a unique organization. Here are key techniques through which this combination can enhance adequacy.
The Fusion of Soft Skills Training with Generative AI
By merging the power of soft skills, generative AI, and IA capabilities, organisations can harness the collective strengths of these elements to establish a dynamic partnership. Here are key methods through which this fusion can amplify effectiveness:
1. Elevated Decision Making -
Delicate abilities, enveloping basic investigation, instinct, and profound keenness, engage people to explore unpredictable decisions informed by different factors, including setting, values, and moral contemplations. Generative simulated intelligence, driven by cutting-edge profound learning calculations, can take apart broad information, perceive designs, and figure out creative goals. IA can then mechanize the execution of these decisions. By joining generative man-made intelligence and IA with human dynamic methods, associations can achieve more edified, creative, and proficient choices, bringing about superior results and increased adequacy.
2. Intelligent Automation and Ingenuity -
While IA succeeds in computerising normal and redundant assignments, it can likewise consolidate synergistic with generative computer-based intelligence to enhance imagination and creativity. Generative simulated intelligence models, like calculations for text or picture creation, can produce novel substance, ideas, or outlines that people can in this manner refine and take advantage of. Through the reconciliation of generative computer-based intelligence, associations can smooth out activities and channel the inventiveness of the two people and machines, prompting increased viability and spearheading arrangements working closely together.
3. Tailored Patron Experiences -
Delicate abilities hold a critical job in getting a handle on and taking care of client requirements. IA can individualise supporter encounters for an expansive scope. By taking apart client information and tendencies, generative artificial intelligence models can form customised suggestions, messages, or item choices. IA can then robotise the spread of these modified encounters across different stages. The combination of delicate abilities, generative simulated intelligence, and computerisation enables associations to administer tailor-made encounters to clients, intensifying satisfaction, loyalty, and at last, business adequacy.
4. Collaboration and Innovation -
Proficient coordinated effort and development stand as key parts for pushing business win. Delicate abilities like correspondence, collaboration, and innovativeness encourage a climate of cooperative energy where thoughts can stream uninhibited, and grouped perspectives can blend. Generative simulated intelligence models can work with ideation by conjuring new ideas, situations, or models. IA stages can then automate the joint effort processes, guaranteeing smooth-out correspondence, documentation, and iterative input. By outfitting delicate abilities and IA, associations can develop coordinated efforts, facilitate advancement, and acknowledge outlook-changing achievements, all while improving viability.
Embracing the Advancing Future Generative AI
Consolidating delicate abilities and IA presents significant potential, inciting associations to be aware of the movements ahead. A few pivotal perspectives merit consideration:
Addressing Challenges and Seizing Opportunities in the Softskills Training Industry
I. Ensuring Data Accuracy and Fairness
The viability of generative man-made intelligence models depends on information for inventive results. Ensuring the quality, assortment, and fair-mindedness of preparing information is basic. Inclinations inside this information can stretch out to generative simulated intelligence results, yielding accidental repercussions. Associations ought to execute solid information administration and moral norms to handle these issues, guaranteeing judicious work of generative man-made intelligence.
II. Fostering Human AI Interaction and Confidence
Accomplishing amicable cooperative energy including delicate abilities, generative artificial intelligence, and IA is dependent on powerful joint effort and trust among people and computer-based intelligence frameworks. Developing a milieu that energizes straightforward correspondence and learning among human specialists and computer-based intelligence innovation is fundamental. This includes outfitting and preparing to acquaint representatives with simulated intelligence abilities, limits, and moral contemplations. Developing confidence in computer-based intelligence frameworks engages workers to team up capably with IA, improving efficiency and results.
III. Navigating Ethical and Legal Ramifications
The rising refinement of generative man-made intelligence presents moral and legitimate intricacies. Associations should wrestle with worries like licensed innovation freedoms, protection issues, and possible abuse of generative artificial intelligence. Creating clear-cut arrangements, complying with appropriate guidelines, and advancing dependable IA use stand as significant measures to moderate dangers.
Conclusion:
The intermingling of delicate abilities and IA offers associations a huge opportunity to improve productivity, empower development, and give excellent client encounters. By utilizing human qualities, the innovative parts of generative computer-based intelligence, and the productivity of IA, ventures can go with informed decisions, mechanize errands, advance joint effort, and achieve amazing results. Notwithstanding, this excursion requests insightful preparation, moral examination, and a culture of human-simulated intelligence collaboration.
As the business climate advances, associations should embrace the capability of consolidating delicate abilities and IA to keep up with seriousness and prosper in the computerized age.
Prepared to open the genuine capability of joining delicate abilities, generative artificial intelligence, and IA? Reach out to us today to investigate generative artificial intelligence-based corporate delicate abilities preparing that can drive your improved efficiency of workers, and encourage feasible development. How about we cooperate to shape the future and make unmatched progress in the computerized period.
The post Generative AI in the Corporate World: Unlocking Promise and Overcoming Challenges appeared first on 333dots it consulting in frisco.
]]>The post UNDERSTANDING DEVOPS PRACTICES appeared first on 333dots it consulting in frisco.
]]>What is DevOps?
It’s a popular expression, certainly. It’s a training. It’s a cycle. It’s a culture. It’s a device set. It’s those things, and that’s only the tip of the iceberg. Some of the time, its definition will change contingent upon who you ask and what issues their association faces. What won’t ever change? A definitive point of DevOps is to assist associations with conveying better programming items quickly.
In the conventional programming advancement process, engineers discount code and hand it to IT administrators to run. In any case, both turn of events and IT activities groups needed to improve on this handoff. This is the manner by which DevOps rehearses arose. Similarly, as the Spry declaration tested customary programming advancement techniques, the DevOps development tested how groups were delivering that product. What’s more, out of these essential thoughts, we have seen progressive changes in advances and societies that have affected how we configuration, fabricate and oversee programming today.
How it Functions
DevOps practically speaking works at tending to two regions:
1. Organizational culture, and
2. The product pipeline itself.
Changing Organizational Culture
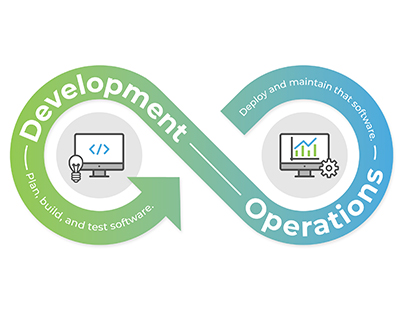
The expression “DevOps” itself is a blend of “improvement” and “tasks.” In customary authoritative designs, these two teaches once in a blue moon, if at any point, speak with one another. DevOps separates the storehouses of these two disciplines. As DevOps rehearses have developed, groups working inside this system look to separate storehouses across ALL disciplines who add to building programming items. This incorporates creators, security engineers, planners, information science investigators, from there, the sky is the limit. Anybody who is engaged with the item lifecycle, from ideation to creation and then some. Changing hierarchical culture is the first (and typically the hardest) step.
Optimizing the Product Pipeline Process
Since DevOps rehearses assist groups with conveying greater programming items quicker, streamlining the item pipeline process envelops everything from ideation to overseeing and checking the item underway. DevOps looks to bring adequacy and efficiencies up in all areas.
Here are some ways that DevOps practices can improve the product pipeline:
• Expanded income
• Lower functional and above cost
• Essentially more limited chance to-advertise
• Further developed consumer loyalty
• Better item quality
• Further developed efficiency and productivity
• Expanded cooperation and worker fulfillment
• Further developed security incorporation
Putting it Into Practice
All in all, what are a few useful advances that an association can take to start profiting from DevOps? In this part we’ve recorded a portion of the center occupants of any DevOps procedure, what they are, and for what reason they’re significant. The thoughts we’ll cover here are:
1. Collaborating and Sharing Knowledge
2. Identifying and Simplifying Processes
3. Automating Processes
4. Monitoring Success and Failures
Collaborating and Sharing Knowledge

Nobody will have every one of the responses. Regardless of whether somebody, no organization can use their time and assets successfully if by some stroke of good luck one or a small bunch of individuals hold the keys to the information safe. For anything to be versatile past a solitary human’s work, other colleagues need to have the information as well. Along these lines, they can rehash the interaction freely.
A decent beginning spot for building or redoing an information base is to begin with a rundown of inquiries to respond to. Each group has their own arrangement of inquiries they need responded to suitably go about their responsibilities. Assembling that large number of inquiries in a brought together area can establish the groundwork for documentation that groups see as valuable. Joint effort can begin to become an integral factor as we work with each group to begin responding to those inquiries.
One way we’ve viewed as compelling at getting colleagues to furnish us with their arrangements of inquiries is posing to them “In the event that we let you know that we expected to you to perform task X at the present time, what questions promptly jump into your head?”
For a more substantial model, at 333 Dots, every item we fabricate is one of a kind in the administrations it gives and the difficulties it defies (and tackles). In any case, in spite of their uniqueness, they all offer specific commonalties — questions we realize we should deal with serious consequences regarding each task. Questions like:
• Where will we store the source code?
• How will we deploy the product locally?
• How will we deploy the code?
• What resources does this code need to run in production?
• Where will our application logs live and how will we access them?
• What security concerns do we have?
• What kind of metrics should we be collecting?
Fostering an information-sharing society is the initial step in light of the fact that each step after it possibly works assuming there’s an effective technique set up to show individuals how to utilize it. What we construct may be a special snowflake. The manner in which we construct doesn’t need to be.
Identifying and Simplifying Processes
To address an item pipeline from ideation to the board and observing underway, a reasonable image of that pipeline is fundamental. To make that image, various disciplines need to cooperate to recognize the many advances required in route. This can transform into a superb practice in recognizing holes and superfluous intricacies. It’s just when you can understand the situation completely from beginning to end that the openings become evident; it’s far-fetched that you’ll see a unique piece is missing in the event that you haven’t assembled the vast majority of the riddle.
Identifying and simplifying processes is also a crucial first step to automating anything for one simple reason: you can’t automate what doesn’t exist. If you don’t know what your process is, you’re going to have a very difficult time programming something to run it for you.

Suppose you realize that you need to computerize the form cycle for your application. Do you be aware when in the process the robotization gets set off? Will it happen each time an engineer commits any kind of code to your storehouse? Does code should be explored and supported first? How might code be surveyed and endorsed?
While you’re thinking about robotizing organizations, do you have any idea what your rollback procedure will be assuming something turns out badly? How do arrangements get set off? Who should be informed? How might they be told?
Similarly, with rearrangements, the main thing more terrible than endeavoring to work with an excessively mind-boggling process is endeavoring to robotize an excessively intricate cycle. More intricacies mean more expected weak spots. That implies additional time spent investigating your computerization apparatuses than profiting from them.
Carve out the opportunity to guarantee your cycles are as perfect as possible prior to attempting to mechanize them. Believe us.
Automating Processes

Presently for the truly cool part. This is where the difficult work of getting various groups to converse with one another begins to pay off. Presently you take components from that large number of disciplines and apply it to the sort of work that everybody likes to gloat about.
Engineers can work with IT administrators to set up servers and occupations that let them filter their code for quality issues or construct their product consequently from source code. Security groups can set and authorize principles with Static Application Security Testing (SAST) devices. You can begin setting up designated spots that never again depend as much on human cooperation, and that implies you can start to decrease bottlenecks and open doors for human blunder.
Obviously, this is certainly not a short-term shift. While there are innumerable apparatuses set up to help these undertakings, you actually need to interface these devices to help your particular task needs. That actually requires some investment. What’s more, frequently a Ton of experimentation.
Monitoring
The following stage — measurements. How would you know your application is working? Where do you have any idea when something veers off-track? What might be said about the times when you’re not permitted to get to your creation climate for security or potentially consistence reasons?
We frequently utilize “send off” to discuss conveying our applications to creation. Assuming we proceed with that similarity, when NASA dispatches a test to Mars, they’re working under the expectation that they’re never going to have the option to contact that machine once more. They need to incorporate all necessary devices to comprehend the test’s wellbeing and execution before it advances toward the stars.
We realize that variables beyond our reach might affect how the application is running. By watching out for the result, you can stay careful with least exertion. The moment something isn’t running as it ought to, you can move right into it with an issue arrangement outlook.

In Summary
Executing DevOps rehearses all through a whole association is troublesome, and it requires investment. In any case, we accept that the work and speculation is at last worth the effort. The verification, as is commonly said, is in the pudding. Building better items quicker implies everybody wins.
The post UNDERSTANDING DEVOPS PRACTICES appeared first on 333dots it consulting in frisco.
]]>The post Protect Yourself Online: 6 Essential Tips for Enhanced Cyber Security Awareness appeared first on 333dots it consulting in frisco.
]]>6 Essential Tips for Enhanced Cyber Security Awareness
In today’s interconnected world, the Internet serves as a gateway to information, communication, and endless opportunities. From conducting business transactions to connecting with friends and family, our lives have become deeply intertwined with the digital realm. However, with this convenience comes the looming threat of cybercrime. Every click, swipe, and tap leaves us vulnerable to hackers, identity thieves, and malicious software. In such a landscape, it’s imperative to prioritize cyber security and take proactive steps to safeguard our digital lives. In this blog, we’ll explore 6 essential tips to enhance your cyber security awareness and protect yourself online.
1. Strengthen Your Digital Fortress with Strong Passwords
Let’s begin with the cornerstone of cyber security: passwords. Think of them as the keys to your digital kingdom. Unfortunately, many people still resort to using weak, easily guessable passwords like “password123” or “123456,” unknowingly leaving their online accounts susceptible to attacks. In an age where hackers employ sophisticated techniques to crack passwords, relying on such simplistic combinations is akin to leaving your front door wide open.
So, what constitutes a strong password? Well, it’s all about complexity and uniqueness. Aim for a mix of uppercase and lowercase letters, numbers, and special characters. Steer clear of using predictable information like your name, birth date, or pet’s name, as these can be easily guessed or gleaned from your social media profiles. Instead, opt for a passphrase that holds personal significance but remains cryptic to others.

Consider leveraging password management tools like LastPass or Dashlane to generate and securely store complex passwords for all your accounts. These tools not only eliminate the hassle of remembering multiple passwords but also ensure each one is unique and virtually uncrackable. By fortifying your digital fortress with strong passwords, you erect a formidable barrier against unauthorized access and protect your sensitive information from prying eyes.
” Cyber-Security is much more than a matter of IT “
2. Double Down on Security with Two-Factor Authentication (2FA)
While robust passwords provide a solid line of defense, adding an extra layer of security never hurts. Enter two-factor authentication (2FA), a powerful tool that bolsters the protection of your online accounts by requiring not just one, but two forms of verification. In addition to entering your password, you’ll need to provide a second factor of authentication, such as a unique code sent to your mobile device, a fingerprint scan, or a security key.
Enabling 2FA adds a hurdle for would-be attackers, even if they manage to obtain your password through illicit means. Many popular online services, including Google, Facebook, and Microsoft, offer 2FA as an optional security feature. Take advantage of it wherever possible to fortify the defenses of your most critical accounts and thwart unauthorized access attempts.


3. Stay One Step Ahead: Keep Your Software and Devices Updated
Software updates may seem like a nuisance, constantly clamoring for your attention with promises of bug fixes and performance improvements. However, beneath their seemingly mundane façade lies a crucial component of cyber security. Developers routinely release updates to patch security vulnerabilities and address known issues that could be exploited by cybercriminals.
By neglecting these updates, you leave your devices and software vulnerable to exploitation, effectively rolling out the red carpet for cyber attackers. Make it a habit to regularly check for and install updates across all your devices, including your computer, smartphone, tablet, and even your internet-connected smart appliances. Enable automatic updates wherever possible to ensure you’re always running the latest, most secure versions of your software.
Additionally, don’t overlook the importance of keeping your antivirus and anti-malware programs up to date. These essential tools serve as your digital watchdogs, tirelessly scanning for and neutralizing threats lurking in the digital shadows. By staying one step ahead of cybercriminals through timely updates, you fortify your defenses and safeguard your digital domain against potential intruders.
4. Exercise Caution: Beware of Phishing Attempts
In the murky waters of cybercrime, phishing remains a perennial threat, casting its deceptive lures in the hopes of ensnaring unsuspecting victims. Phishing attacks typically take the form of fraudulent emails, messages, or websites masquerading as legitimate entities, such as banks, social media platforms, or government agencies. Their goal? To trick you into divulging sensitive information like login credentials, credit card numbers, or personal details.
To avoid falling victim to phishing scams, exercise caution and skepticism when encountering unsolicited emails or messages, especially those urging immediate action or conveying a sense of urgency. Take a closer look at the sender’s email address or domain name for any discrepancies or irregularities that may betray its fraudulent nature. When in doubt, err on the side of caution and refrain from clicking on any suspicious links or downloading attachments from unknown sources.
Remember, reputable organizations will never request sensitive information via email or text message, nor will they pressure you into disclosing personal details hastily. When in doubt, verify the legitimacy of the communication by reaching out to the organization directly through official channels. By remaining vigilant and discerning, you can effectively thwart phishing attempts and safeguard your valuable information from falling into the wrong hands.


5. Fortify Your Digital Perimeter: Secure Your Wi-Fi Network
Your home Wi-Fi network serves as the gateway to your digital kingdom, facilitating seamless connectivity and communication across all your devices. However, if left unprotected, it can also serve as a vulnerable entry point for cyber attackers seeking to infiltrate your network and compromise your devices.
To fortify your digital perimeter and safeguard your Wi-Fi network against intruders, start by changing the default username and password for your router to a strong, unique combination. Avoid using easily guessable passwords or phrases that could be cracked through brute force attacks. Instead, opt for a passphrase that combines randomness with personal significance, making it virtually impervious to unauthorized access.
Next, ensure your Wi-Fi network is encrypted using the latest security protocols, such as WPA2 or WPA3, to encrypt the data transmitted between your devices and the router. Disable any outdated or vulnerable features like Wi-Fi Protected Setup (WPS), as they can serve as potential entry points for attackers. Finally, regularly update your router’s firmware to patch any known security vulnerabilities and ensure it remains resilient against emerging threats.
By fortifying your Wi-Fi network and securing your digital perimeter, you create a robust defense against unauthorized access and protect your devices from potential intrusions.
6. Practice Digital Diligence: Mindful Online Behavior
Last but certainly not least, your online behavior plays a pivotal role in your cyber security posture. In an era marked by unprecedented connectivity and digital interaction, exercising mindfulness and diligence is paramount to safeguarding your digital well-being.
Avoid clicking on suspicious links or downloading files from untrusted sources, as they may harbor malware or lead to phishing websites designed to steal your personal information. Be cautious when sharing sensitive information online, especially on social media platforms, and adjust your privacy settings to limit who can view your posts and profile information.
Furthermore, practice good digital hygiene by logging out of accounts when not in use, especially on shared or public devices. Routinely review your account activity for any signs of unauthorized access or suspicious behavior, and promptly report any anomalies to the respective platform or service provider.
By cultivating a culture of digital diligence and mindfulness, you empower yourself to navigate the digital landscape safely and securely, minimizing the risk of falling victim to cybercrime.

In conclusion, cyber security awareness is not merely a passive pursuit but an ongoing journey of vigilance, education, and empowerment. By implementing these six essential tips, you can enhance your cyber security posture and protect yourself against the ever-evolving threat landscape of the digital world. Remember, your digital safety is in your hands—empower yourself, stay informed, and stay safe online.
The post Protect Yourself Online: 6 Essential Tips for Enhanced Cyber Security Awareness appeared first on 333dots it consulting in frisco.
]]>The post EMPOWERING BUSINESSES IN FRISCO: 333 DOTS IT CONSULTING & TRAINING SERVICE appeared first on 333dots it consulting in frisco.
]]>IT Consulting & Training in Frisco: Empowering Businesses with Best-in-Class Solutions
In today’s fast-paced digital world, businesses are constantly seeking ways to stay ahead of the competition and maximize their efficiency. One of the key factors that contribute to their success is the effective utilization of Information Technology (IT) solutions. However, with the ever-evolving technology landscape, it can be challenging for businesses to keep up with the latest trends and ensure IT infrastructure security. This is where Frisco’s IT consulting and training services come into play, providing businesses with the expertise and guidance they need to thrive in the digital age.

Frisco, a vibrant city in Texas, has emerged as a hub for IT consulting and training services. With its booming economy and a strong focus on technology, 333 Dots offers businesses a wide range of options when it comes to IT consulting and training. Whether it’s implementing cloud solutions, enhancing network security, or providing cyber security services, 333 Dots has become a go-to destination for businesses looking to leverage IT for their growth.
When it comes to IT consulting and training services in Frisco, one name stands out – the 333 Dots Best IT Training & Consulting Service in Frisco. With a team of highly skilled professionals and a track record of delivering exceptional results, they have become the preferred choice for businesses in the region. Their comprehensive suite of services covers a wide range of IT solutions, including AWS Cloud Security, network security, AWS Cloud, cloud proxy, and cyber security.


AWS Cloud Security is a critical aspect of modern IT infrastructure. As businesses increasingly rely on cloud-based solutions, ensuring the security of their data and applications becomes paramount. The 333 Dots Best IT Training & Consulting Service in Frisco specializes in providing AWS Cloud Security solutions, helping businesses protect their sensitive information and mitigate the risks associated with cloud computing. From implementing robust access controls to monitoring and detecting potential threats, their expertise in AWS Cloud Security ensures that businesses can leverage the benefits of the cloud without compromising on security.
Network security is another area where businesses need to stay vigilant. With the increasing number of cyber threats and the growing complexity of networks, ensuring the integrity and confidentiality of data has become a top priority. The 333 Dots Best IT Training & Consulting Service in Frisco offers comprehensive network security solutions, including firewall implementation, intrusion detection systems, and vulnerability assessments. By partnering with them, businesses can strengthen their network security posture and minimise the risk of data breaches.
Network security is another area where businesses need to stay vigilant. With the increasing number of cyber threats and the growing complexity of networks, ensuring the integrity and confidentiality of data has become a top priority. The 333 Dots Best IT Training & Consulting Service in Frisco offers comprehensive network security solutions, including firewall implementation, intrusion detection systems, and vulnerability assessments. By partnering with them, businesses can strengthen their network security posture and minimize the risk of data breaches.


In addition to AWS Cloud Security and network security, the Best IT Training & Consulting Service in Frisco also specializes in AWS Cloud solutions. With the scalability and flexibility offered by AWS Cloud, businesses can optimize their IT infrastructure and reduce costs. The team at 333 Dots Best IT Training & Consulting Service in Frisco helps businesses migrate their applications and data to the cloud, ensuring a seamless transition and maximizing the benefits of AWS Cloud.
Cloud proxy is another area where businesses can benefit from 333 Dots IT consulting and training services in Frisco. A cloud proxy acts as an intermediary between users and the internet, providing an additional layer of security and control. By implementing a cloud proxy solution, businesses can monitor and filter internet traffic, block malicious websites, and enforce corporate policies. The 333 Dots Best IT Training & Consulting Service in Frisco offers expertise in cloud proxy solutions, helping businesses enhance their security posture and protect against cyber threats.


Cyber security is a growing concern for businesses of all sizes. With the increasing sophistication of cyber-attacks, businesses need to be proactive in protecting their sensitive information. The 333 Dots Best IT Training & Consulting Service in Frisco offers a range of cyber security services, including vulnerability assessments, penetration testing, and incident response. By partnering with them, businesses can identify and address vulnerabilities in their IT infrastructure, ensuring the confidentiality, integrity, and availability of their data.
In conclusion, 333 Dots IT consulting and training services in Frisco play a crucial role in empowering businesses with best-in-class IT solutions. Whether it’s AWS Cloud Security, network security, AWS Cloud, cloud proxy, or cyber security, 333 Dots Best IT Training & Consulting Service in Frisco offers businesses the expertise and guidance they need to navigate the complex world of IT. By leveraging their services, businesses can enhance their security posture, optimize their IT infrastructure, and stay ahead of the competition in today’s digital age.
The post EMPOWERING BUSINESSES IN FRISCO: 333 DOTS IT CONSULTING & TRAINING SERVICE appeared first on 333dots it consulting in frisco.
]]>